What is Cisco SD-WAN NAT DIA Feature
Cisco SD-WAN offers a powerful feature called Direct Internet Access (DIA). DIA is a component of the Cisco SD-WAN architecture that enables certain traffic from branch locations to route directly to the Internet by performing NAT, bypassing the organization’s data center. By doing so, it reduces latency and improves application performance for Internet-bound traffic.
Benefits of Using DIA:
- Reduced Latency: By avoiding route through the data center, DIA ensures faster access to Internet resources.
- Improved Application Performance: Applications that rely on the Internet experience better responsiveness.
- Cost Optimization: DIA allows organizations to use a mix of MPLS (Multiprotocol Label Switching) and low-cost broadband or other transports in an active/active fashion, optimizing capacity and reducing bandwidth costs. Also this reduction of load on Data Center’s Circuits.
Methods to Implement NAT DIA
Cisco SD-WAN provides below methods to implement NAT DIA
- Static NAT Route: Configure a static NAT route to direct traffic from the service VPN to the Internet. This method diverts all traffic to NAT DIA for which specific route is not available in particular service VPN.
- Centralized Data Policy: Create a centralized data policy that matches traffic from the service VPN and sets the NAT for VPN0 (DIA). This method uses various configured parameters(like source/destination/application etc) to match and divert the traffic to NAT DIA, thus provides more granularity.
- Cloud On Ramp (CoR) for SaaS: Cisco SD-WAN provides option to configure CoR SaaS applications which can leverage NAT DIA or Gateway exit to reach SaaS applications.
In this article, we will use Static NAT Route method to configure NAT DIA. Later will explore Centralised Data Policy / CoR SaaS method in another article.
Topology
We will be using below topology for this demonstration. Here we have two Service VPNs – VPN10 and VPN20. We will be enabling DIA exit for users in VPN10.
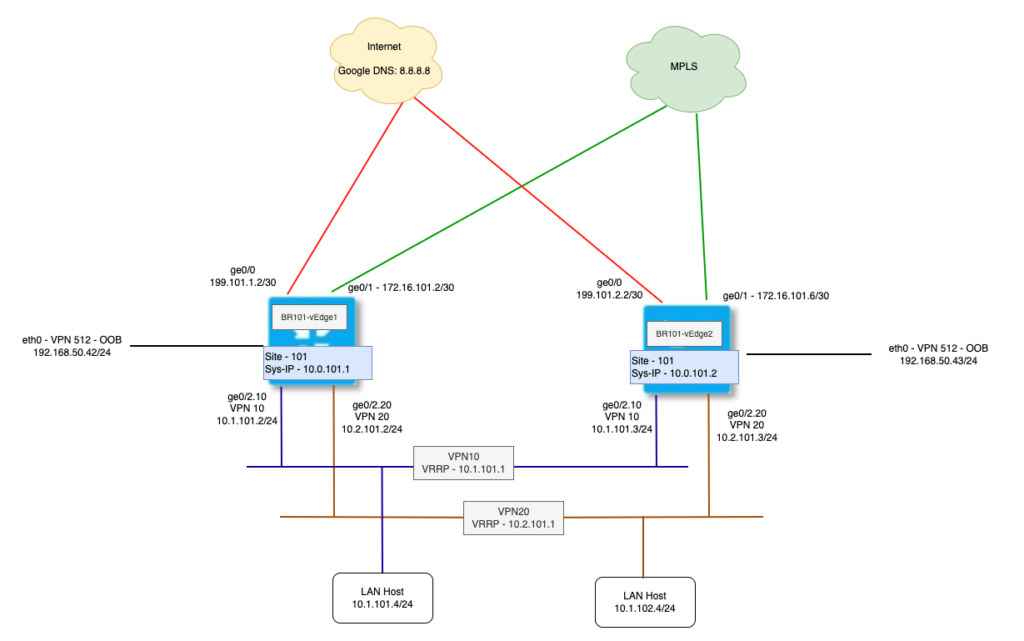
Configuration
Configuring NAT DIA for VPN10 require two steps.
- Configure NAT statement on Internet Interface.
- Configure Static NAT route in VPN10
Steps
1. Identify Device Template name on vManage GUI via Configuration > Devices and search for Device.

2. Navigate to Configuration > Template > Device Template and view identified Device Template to find the Feature Template name for VPN 0 Internet Interface and VPN10 template.

3. Navigate to Configuration > Template > Feature Template. Edit above Feature Template and Enable NAT. You can change other parameters of NAT if required. Once done, click update.

4. Now these changes will be pushed to all attached devices having the Feature template. Click Next and move to check configuration differences. Once ready, click Configure.

5. Once above configuration pushed, edit VPN10 Feature Template to add Static NAT route. In IPv4 Route section, add new IPv4 route.


6. Update Feature template and check configuration differences and push configuration to devices.

7. Login to configured devices CLI and you will see a new Default Static NAT route in VPN10 table.
BEFORE
BR101-vEdge-1# sh ip route vpn 10
Codes Proto-sub-type:
IA -> ospf-intra-area, IE -> ospf-inter-area,
E1 -> ospf-external1, E2 -> ospf-external2,
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2,
e -> bgp-external, i -> bgp-internal
Codes Status flags:
F -> fib, S -> selected, I -> inactive,
B -> blackhole, R -> recursive, L -> import
PROTOCOL NEXTHOP NEXTHOP NEXTHOP
VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS
---------------------------------------------------------------------------------------------------------------------------------------------
10 10.1.10.0/30 omp - - - - 10.0.10.1 mpls ipsec F,S
10 10.1.10.0/30 omp - - - - 10.0.10.1 biz-internet ipsec F,S
10 10.1.10.4/30 omp - - - - 10.0.10.2 mpls ipsec F,S
10 10.1.10.4/30 omp - - - - 10.0.10.2 biz-internet ipsec F,S
10 10.1.101.0/24 connected - ge0/2.10 - - - - - F,S
10 192.168.10.10/32 omp - - - - 10.0.10.1 mpls ipsec F,S
10 192.168.10.10/32 omp - - - - 10.0.10.1 biz-internet ipsec F,S
10 192.168.10.10/32 omp - - - - 10.0.10.2 mpls ipsec F,S
10 192.168.10.10/32 omp - - - - 10.0.10.2 biz-internet ipsec F,S
AFTER
BR101-vEdge-1# sh ip route vpn 10
Codes Proto-sub-type:
IA -> ospf-intra-area, IE -> ospf-inter-area,
E1 -> ospf-external1, E2 -> ospf-external2,
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2,
e -> bgp-external, i -> bgp-internal
Codes Status flags:
F -> fib, S -> selected, I -> inactive,
B -> blackhole, R -> recursive, L -> import
PROTOCOL NEXTHOP NEXTHOP NEXTHOP
VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS
---------------------------------------------------------------------------------------------------------------------------------------------
10 0.0.0.0/0 nat - ge0/0 - 0 - - - F,S
10 10.1.10.0/30 omp - - - - 10.0.10.1 mpls ipsec F,S
10 10.1.10.0/30 omp - - - - 10.0.10.1 biz-internet ipsec F,S
10 10.1.10.4/30 omp - - - - 10.0.10.2 mpls ipsec F,S
10 10.1.10.4/30 omp - - - - 10.0.10.2 biz-internet ipsec F,S
10 10.1.101.0/24 connected - ge0/2.10 - - - - - F,S
10 192.168.10.10/32 omp - - - - 10.0.10.1 mpls ipsec F,S
10 192.168.10.10/32 omp - - - - 10.0.10.1 biz-internet ipsec F,S
10 192.168.10.10/32 omp - - - - 10.0.10.2 mpls ipsec F,S
10 192.168.10.10/32 omp - - - - 10.0.10.2 biz-internet ipsec F,S
BR101-vEdge-1# 8. Generate traffic to test DIA exit from LAN device.
LAB125-LAN-Router#ping vrf br101-vrf10 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
LAB125-LAN-Router#9. BR101-vEdge-1 is VRRP active and it shows NAT translation.
BR101-vEdge-1# show ip nat filter
PRIVATE PRIVATE PRIVATE PRIVATE PUBLIC PUBLIC PUBLIC
NAT NAT SOURCE DEST SOURCE DEST SOURCE PUBLIC DEST SOURCE DEST FILTER IDLE OUTBOUND OUTBOUND INBOUND INBOUND
VPN IFNAME VPN PROTOCOL ADDRESS ADDRESS PORT PORT ADDRESS ADDRESS PORT PORT STATE TIMEOUT PACKETS OCTETS PACKETS OCTETS DIRECTION
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0 ge0/0 10 icmp 10.1.101.4 8.8.8.8 5 5 199.101.1.2 8.8.8.8 5 5 established 0:00:00:02 5 590 5 570 -
CLI Configuration
vpn 0
interface ge0/0
ip address 199.101.1.2/30
nat <<<<<<<<vpn 10
ip route 0.0.0.0/0 vpn 0 <<<<<<<<This completes NAT DIA configuration on vEdge router. For more details, please refer Cisco Documentation.

Once again you nailed down the complicated terminology of SDWAN into easy to understand words.
Thank you Pradeep !!!