Table of Contents
In last article, we discussed NAT DIA on vEdge using Static NAT route. Now let’s explore other option to implement NAT DIA i.e via Centralized Data Policy Method. Refer that article for benefits of NAT DIA.
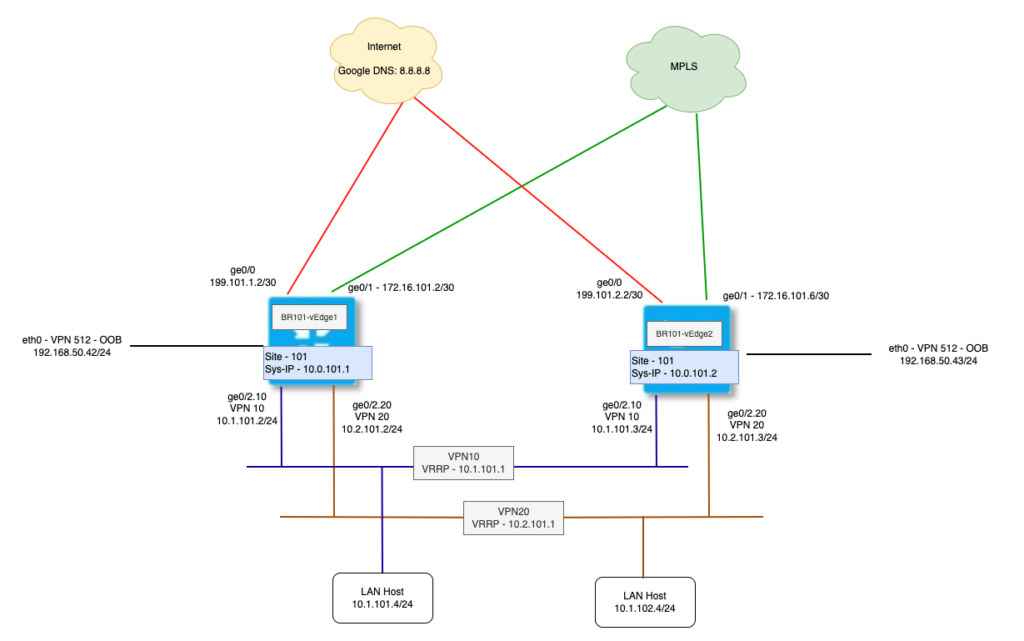
Topology
We are going to use same topology as in last article. We had implemented NAT DIA with Static NAT route in Service VPN 10. Now we will implement NAT DIA using Centralized Data Policy in Service VPN 20.
Configuration
Centralized Data Policy provided full flexibility to re-direct traffic based on multiple factors like Source-IP, Destination-IP, Application Type, Protocol etc. If we use this method, then traffic follows the defined action and doesn’t anymore depends on route-table lookup. This can be compared to PBR(Policy Based Routing) in IOS-XE Autonomous mode.
Note, Centralised policy is applied via vSmarts and vManage requires all vSmarts in vManage Mode (i.e. Template attached) to activate Centralized Policy. If vSmarts are not having template attached, then first attach a template to them.
Steps
1. Navigate to Configuration > Policies. Under Centralized Policy, click Add Policy.

2. First step is “Create group of Interest”. Here you can create list of different objects(like Data Prefix, Site, VPN, Application etc.) to match the desired traffic or use existing lists. For this demonstration, I am re-directing Google-Apps and Dropbox traffic via DIA path using Centralized Data Policy.
- Both Google-Apps & Dropbox applications are pre-defined on vManage GUI. If you need some specific application not listed, create a new application list.

- Create a Site-list to which the policy will be applied. I am going to apply this to site 101.

- Create VPN list to which this policy will be applied. I am using VPN 20.

3. Click Next two times and move to option “Configure Traffic Rules”. Select Traffic Data and click Add Policy > Create New.

4. Provide a Name & Description for this policy. Click create Sequence Type and choose Custom.

5. Click Sequence Rule to create a new sequence. Click “Application/Application Family List” and choose “Google_Apps”. You can also match other options like source-prefix etc.

6. Click Action. Choose Accept and NAT VPN. You can also choose other actions as desired. I have also added Counter option which will give counters of matching traffic. Once done, click Save Match and Actions to save the rule.

7. Similarly define other rules as needed. Once done, make sure to Accept the traffic in Default Sequence. Save the policy.

8. Click Next to Navigate to Next option of wizard – Apply Policy to Sites and VPNs. Provide Name & Description to Centralized Policy and choose options as per below image. Once done, hit preview and save the policy.

Config-Preview
viptela-policy:policy
data-policy _VPN20_Select-DIA-Policy
vpn-list VPN20
sequence 1
match
app-list Google_Apps
source-ip 0.0.0.0/0
!
action accept
nat use-vpn 0
count Google-apps-counters_1336674583
!
!
sequence 11
match
app-list dropbox_apps
source-ip 0.0.0.0/0
!
action accept
nat use-vpn 0
count dropbox-counters_1336674583
!
!
default-action accept
!
lists
app-list Google_Apps
app google_translate
app google-earth
app google_docs
app google-services-audio
app google_picasa
app google-photos
app google_appengine
app hangouts-media
app google_cache
app google-meet-audio
app gtalk-chat
app google-services-media
app gmail_mobile
app gmail
app google_plus
app google-chat
app hangouts-audio
app ytimg
app youtube_hd
app google-meet-video
app google_gen
app google-services
app gtalk-ft
app google_trusted_store
app google
app hangouts-chat
app google-services-video
app google-accounts
app google_maps
app gmail_chat
app google_groups
app google-docs
app googlebot
app google_play_music
app google_photos
app chrome_update
app google-meet-media
app google_desktop
app google_tags
app google_safebrowsing
app google_earth
app google_play
app google_sprayscape
app google-plus
app picasa
app gtalk-video
app google_ads
app android-updates
app gcs
app google_analytics
app google_code
app google_toolbar
app blogger
app hangouts-video
app google_weblight
app gtalk
app gmail_basic
app google_calendar
app google-meet
app google_accounts
app gmail_drive
app google_classroom
app hangouts
app gstatic
app google-play
app google_spaces
app gtalk-voip
app google_skymap
app hangouts-file-transfer
app google-downloads
app youtube
app google_localguides
!
app-list dropbox_apps
app dropbox
app dropbox_upload
!
site-list Site101
site-id 101
!
vpn-list VPN20
vpn 20
!
!
!
apply-policy
site-list Site101
data-policy _VPN20_Select-DIA-Policy from-service9. Click options of newly created Centralised Policy and Activate.

10. Review the configuration being pushed to vSmarts and Activate.
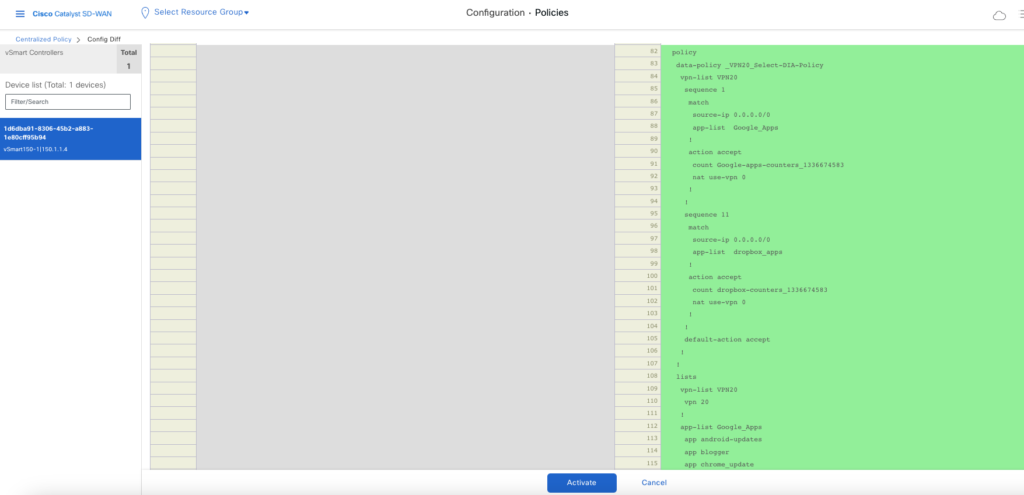
11. Once policy successfully activate, you can check policy pushed from vSmart to Site101 vEdges.
BR101-vEdge1
BR101-vEdge-1# show policy from-vsmart
from-vsmart data-policy _VPN20_Select-DIA-Policy
direction from-service
vpn-list VPN20
sequence 1
match
source-ip 0.0.0.0/0
app-list Google_Apps
action accept
count Google-apps-counters_1336674583
nat use-vpn 0
no nat fallback
sequence 11
match
source-ip 0.0.0.0/0
app-list dropbox_apps
action accept
count dropbox-counters_1336674583
nat use-vpn 0
no nat fallback
default-action accept
from-vsmart lists vpn-list VPN20
vpn 20
from-vsmart lists app-list Google_Apps
app android-updates
app blogger
app chrome_update
app gcs
app gmail
app gmail_basic
app gmail_chat
app gmail_drive
app gmail_mobile
app google
app google-accounts
app google-chat
app google-docs
app google-downloads
app google-earth
app google-meet
app google-meet-audio
app google-meet-media
app google-meet-video
app google-photos
app google-play
app google-plus
app google-services
app google-services-audio
app google-services-media
app google-services-video
app google_accounts
app google_ads
app google_analytics
app google_appengine
app google_cache
app google_calendar
app google_classroom
app google_code
app google_desktop
app google_docs
app google_earth
app google_gen
app google_groups
app google_localguides
app google_maps
app google_photos
app google_picasa
app google_play
app google_play_music
app google_plus
app google_safebrowsing
app google_skymap
app google_spaces
app google_sprayscape
app google_tags
app google_toolbar
app google_translate
app google_trusted_store
app google_weblight
app googlebot
app gstatic
app gtalk
app gtalk-chat
app gtalk-ft
app gtalk-video
app gtalk-voip
app hangouts
app hangouts-audio
app hangouts-chat
app hangouts-file-transfer
app hangouts-media
app hangouts-video
app picasa
app youtube
app youtube_hd
app ytimg
from-vsmart lists app-list dropbox_apps
app dropbox
app dropbox_upload
BR101-vEdge-1# BR101-vEdge2
BR101-vEdge-2# show policy from-vsmart
from-vsmart data-policy _VPN20_Select-DIA-Policy
direction from-service
vpn-list VPN20
sequence 1
match
source-ip 0.0.0.0/0
app-list Google_Apps
action accept
count Google-apps-counters_1336674583
nat use-vpn 0
no nat fallback
sequence 11
match
source-ip 0.0.0.0/0
app-list dropbox_apps
action accept
count dropbox-counters_1336674583
nat use-vpn 0
no nat fallback
default-action accept
from-vsmart lists vpn-list VPN20
vpn 20
from-vsmart lists app-list Google_Apps
app android-updates
app blogger
app chrome_update
app gcs
app gmail
app gmail_basic
app gmail_chat
app gmail_drive
app gmail_mobile
app google
app google-accounts
app google-chat
app google-docs
app google-downloads
app google-earth
app google-meet
app google-meet-audio
app google-meet-media
app google-meet-video
app google-photos
app google-play
app google-plus
app google-services
app google-services-audio
app google-services-media
app google-services-video
app google_accounts
app google_ads
app google_analytics
app google_appengine
app google_cache
app google_calendar
app google_classroom
app google_code
app google_desktop
app google_docs
app google_earth
app google_gen
app google_groups
app google_localguides
app google_maps
app google_photos
app google_picasa
app google_play
app google_play_music
app google_plus
app google_safebrowsing
app google_skymap
app google_spaces
app google_sprayscape
app google_tags
app google_toolbar
app google_translate
app google_trusted_store
app google_weblight
app googlebot
app gstatic
app gtalk
app gtalk-chat
app gtalk-ft
app gtalk-video
app gtalk-voip
app hangouts
app hangouts-audio
app hangouts-chat
app hangouts-file-transfer
app hangouts-media
app hangouts-video
app picasa
app youtube
app youtube_hd
app ytimg
from-vsmart lists app-list dropbox_apps
app dropbox
app dropbox_upload
BR101-vEdge-2# Test Flows
Traffic flow can be tested using simulation on vManage GUI or via real Host at LAN side.
1. vManage GUI Simulation Result.

If we simulate flow of some other traffic which is not configured for DIA path, that shows taking Overlay Path.

2. Traffic Initiated from LAN Host in VRF 20 and can see increment in counters of DP policy. Also “show ip nat filter” shows NAT translation.
BR101-vEdge-2# show policy data-policy-filter
POLICER OOS OOS
NAME NAME COUNTER NAME PACKETS BYTES NAME PACKETS BYTES
-------------------------------------------------------------------------------------------------------------
_VPN20_Select-DIA-Policy VPN20 default_action_count 104561 8413657
dropbox-counters_1336674583 38 14180
Google-apps-counters_1336674583 4284 526668
BR101-vEdge-2# show ip nat filter
PRIVATE PRIVATE PRIVATE PUBLIC PUBLIC PUBLIC
NAT NAT SOURCE PRIVATE DEST SOURCE DEST SOURCE PUBLIC DEST SOURCE DEST FILTER IDLE OUTBOUND OUTBOUND INBOUND INBOUND
VPN IFNAME VPN PROTOCOL ADDRESS ADDRESS PORT PORT ADDRESS ADDRESS PORT PORT STATE TIMEOUT PACKETS OCTETS PACKETS OCTETS DIRECTION
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0 ge0/0 20 tcp 10.101.20.10 72.163.217.102 56597 80 199.101.2.2 72.163.217.102 56597 80 established 0:00:35:51 1 70 1 66 -
0 ge0/0 20 tcp 10.101.20.10 172.217.167.142 57168 443 199.101.2.2 172.217.167.142 57168 443 established 0:00:59:15 23 5777 29 11163 -
0 ge0/0 20 udp 10.101.20.10 74.125.250.129 60020 19302 199.101.2.2 74.125.250.129 60020 19302 established 0:00:00:17 9 594 0 0 -
0 ge0/0 20 udp 10.101.20.10 74.125.250.129 60538 19302 199.101.2.2 74.125.250.129 60538 19302 established 0:00:00:36 7 462 0 0 -
Further reading – Cisco Configuration Guide.
